
Protect Yourself Better When Using Social Networks
In the time I’ve spent trying to help people understand the absolute need for better practices that protect their privacy, I’ve come to understand that many people just are not willing to give up their mainstream social media accounts. It sometimes feels like I could tell someone that each minute on Facebook takes a year off their life and they’d keep using Facebook, anyway.
If you enjoy social media, I highly recommend checking out the list of alternative social networks I have posted HERE and the article I posted HERE. If you still can’t fathom leaving the other, more predatory social networks, then I have some advice for you to make your experience slightly more private and safer.
Why Should You Be Concerned About Privacy on Social Networks?
There are many reasons you should concern yourself about privacy on sites like Facebook, Twitter, Instagram, etc. Aside from the fact that social network interactions have led to people being fired, divorce, ending friendships, mental manipulation, and more, there are a lot of legitimate concerns over the amount of data collected and the security of that data.
Every Website Gets Hacked Eventually

For starters, understand that EVERY large website falls victim to a hack, eventually. There’s no way around it. Large websites with large amounts of users are almost always the targets of big hacks because there is much more to gain in the way of user data and much more damage to cause. If you thought the above reasons to avoid social networks were bad, consider that once they are hacked you could be doxxed, have your identity stolen, or worse. Here are just a few links to prove my point if you’re interested in the receipts:
- How Facebook Was Hacked And Why It's A Disaster For Internet Security
- Twitter’s massive hack: What we know after Apple, Biden, Obama, Musk, and others tweeted a bitcoin scam
- Major WhatsApp Warning: Your WhatsApp May Be Hacked And There’s Nothing You Can Do
- Mark Zuckerberg has his Pinterest account hacked (again)
- LinkedIn breach reportedly exposes data of 92% of users
- TikTok vulnerability left users’ personal data including names, photos and phone numbers at risk of being hacked in latest security flaw
- How we got read access on Google’s production servers
Your Data is Sold
Separate from the idea of your data being shared in a hack, but still related, is the fact that most of these companies sell your data to other companies, too. Let’s consider the Facebook/Cambridge Analytica scandal as a prime example. Essentially, Facebook was selling mountains of data to Cambridge Analytica who would use that data to identify people that would likely vote for the candidate they didn’t want. Once they determined who these free-thinking voters were, they launched target ad campaigns on Facebook to manipulate these people. This is a great example of a social network profiting off of the selling of your data, then that data is used to manipulate how you feel about certain things or to sell you something you don't need. You can safely assume this sort of thing is still happening, too. One aspect of this situation that is commonly overlooked is the fact that they transferred your data to yet another company whose security vulnerabilities could allow said data to be leaked to the public, exposing your information again.
There is big money in selling big data, and every big tech company is doing it. It opens the door for more information leaks and attempts at manipulation and targeting, and you shouldn’t be ok with this practice. By minimizing the data that companies collect about you, you are lowering your chances of being a victim to these sorts of attacks and leaks.
The last example of the selling and misuse of your data I will cover is regarding projects like Google’s Jigsaw and companies like Palantir. These are data-science companies that are using unfathomable amounts of data to target you, manipulate you, and ultimately silence you if they don’t like your tone. Whenever a company is talking about a safer internet, always assume they are actually talking about massive amounts of censorship and surveillance. It’s about control, not any noble cause of which they try to convince you.
The Internet is Permanent

When contemplating whether you should post a certain meme, thought, argument, photo, etc., you should also always consider the fact that the internet is permanent. Remember that photo you posted where you were very obviously drunk at a party? Yeah, that’s not going away. How about that argument you had with someone else on Facebook that got a bit nasty and maybe even embarrassing? Delete your posts if you like, there is still a record of it.
Just because you delete something doesn’t mean it is deleted from that company’s servers. Many times, it simply means you removed it from being visible from the rest of the world. Twitter has your deleted tweets and Facebook your deleted posts and pictures. Since siyes like WayBackMachine exist, your posts are often archived very quickly, leaving a public record of your embarrassing outbursts and moments of weakness. Celebrities and others in the spotlight have often fallen victim to someone digging up some dirt using a site like this and re-sharing it with the world. The things you post never truly go away!
Once again, we find ourselves in yet another scenario where past transgressions on the web can haunt us and have a negative, and even severe, impact on our lives. This fact alone should be enough to convince you to limit the time you spend on social networks and reconsider some of the things you choose to share.
What Can I Do to Limit These Risks?
If you care at all about free speech, privacy, and security, then I once again STRONGLY urge you to consider closing your Facebook, Instagram, TikTok, and Twitter accounts while exploring some more privacy-focused, censorship resistant “alt” tech platforms. If your only argument against these newer platforms is the fact that your friends and family aren’t using them, then I urge you to convince them to all follow you to them! When the day comes that more folks would try to stage a mass exodus, it might eventually cause these heartless big-tech companies to reconsider their actions! If you just can’t see yourself closing your mainstream social network accounts, PLEASE consider incorporating some, if not all, of the privacy practices outlined below.
Here are those links to info about these alt-tech platforms, one last time:
- A simple list of SOME of these platforms
- Why You Should Ditch FB & Twitter and What You Can Replace Them With
Use a VPN
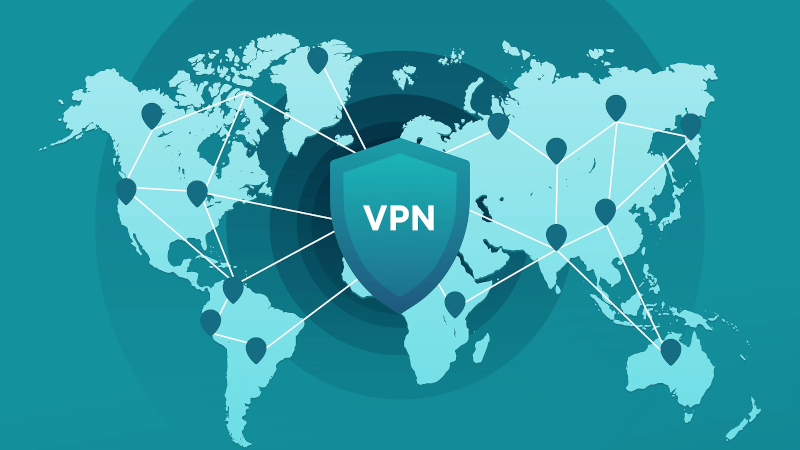
When you use a VPN, your internet traffic is routed through one of your VPN provider’s servers first. A secure, encrypted connection is established between your device and the VPN server. From there, your traffic is routed as usual, but the website or service you connect to will detect your location wherever your VPN server is instead of your actual location. That’s already a small win for your privacy!
Additionally, your traffic is masked so that your ISP (internet service provider) cannot tell what site you are visiting. It’s a well-known fact that many ISPs log your web activity then sell that data. If you stay connected to a VPN, that is the only activity that they can see and everything else you do is your little secret. Again, this prevents your data from being logged, sold, and possibly hacked.
Considering most VPN services only cost a few bucks a month, there is really no reason to not have a VPN service. Almost all of them now have mobile and desktop apps for all platforms. There are other benefits like being able to connect to a VPN server in a certain country to access their television and news. I have a list of VPNs I recommend HERE and an article about them HERE.
Use Different Email Addresses for Different Accounts
If you use the same email address for every account you create, that data can be stitched together to profile you more easily. Twitter can find out what you do on Facebook and vice versa, for example. The more of your data companies can compile together, the better they know how to advertise to you and manipulate your thoughts and feelings.
I highly recommend getting a handful of free email addresses and using them for different things. If your tinfoil hat is as thick as mine, I recommend paying a few bucks a month for an email account with CTemplar. You can designate one as your Instagram email and use it to give out when you think you’ll get spammed. Maybe use another for Pinterest and paying your bills. You can decide how you use all of your email accounts, but I urge you to consider using a unique address for every social network account you create.
I have a list of some more private email services HERE.
Your Photos & Avatar Can Be Used to Track You

Post a lot of photos? Did you know that photos, especially those taken from your phone, contain a ton of data referred to as EXIF (Exchangeable Image File Format) data? The creation of EXIF was to aid photographers in tracking the settings they use for their photos. In the olden days, photographers would use a pen and paper to record things like shutter speed, aperture, ISO speed, time and date of the photo, and more.
Once smartphones arrived, more and more started getting shoved into the EXIF data, but most importantly, GPS coordinates began being put in EXIF data. This means if you post a photo of your new couch or something at home, the coordinates of your home are accessible by others if the EXIF data isn’t removed. Some sites strip this data by default, but many leave it fully intact. If someone out there wanted to stalk or rob you, they could easily get your coordinates from your photos, drop them into a website that turns GPS coordinates into a street address, and know exactly where you live. Even if this unlikely scenario doesn’t play out this way, it is possible and stranger things have and can happen.
This ignores the fact that the site you upload photos to might collect your EXIF data even if they strip it afterward so others can’t get access to it. It’s yet another example of feeding the machine that can be easily avoided.
There are apps for all platforms out there that do nothing more than strip or scramble the EXIF data from the photos you give to it. A simple search online or in the app store of your device should reveal several results for free apps that will take care of this for you. For me, I use ImagePipe from F-Droid and ScrambledExif from the Play Store (downloaded using the Aurora Store to avoid the Play Store) on my de-Googled Android phone. You can find an app like these for iOS and all desktop operating systems as well. Start running your photos through an app like this before you post them.
Last, regarding photos, the avatar/profile pictures you use can be leveraged much like your email address to stitch data from various places together. Make it a habit to use a different photo on every social network or account you sign up for to prevent this.
Never Use Your Actual Name on Social Networks

This one is pretty self-explanatory. You will hear arguments from some influencers that they take people more seriously online when they use their actual names. I can understand this argument to a degree, but remember that these people make a living off of their name or have a brand/image tied to it. If you are just a casual user, you should ABSOLUTELY use an alias online to protect your identity.
Again, not only should you avoid revealing your real name, but much like the idea of using different email addresses and profile pictures I mentioned before, try to use a different alias for every account you sign-up for avoiding having all of your data stitched together.
Never Upload Your Contacts When Prompted

This section is more about protecting the privacy of your friends and family. Many social networks will ask if you want to upload your contacts, and they try to make this sound like a great idea to “make it easier to find your friends”. The issue with this is that you’re giving this social network every detail about that person you have stored in their contact. If you have birthdays, addresses, phone numbers, email addresses, etc in there then you are giving all of that data over for free.
This can be particularly annoying for those you care about as it not only increases the amount of data that big-tech companies have on them, but it can lead to spam emails, calls, and text messages as this data is often sold to anyone willing to pay for it. You also have to consider once again that it will eventually be hacked or leaked as well. If you really care about your friends and family, avoid uploading your contacts and take the extra 5 minutes to find them online manually.
Use a Private Browser Instead of the Mobile Apps

Have you ever looked at the permissions required for the Facebook, Twitter, etc apps to run on your phone or tablet? They basically ask for complete access to every part of your device! It’s excessive and a bit disturbing.
Here are the Facebook app permissions for Android:
This app has access to:
Microphone
- record audio
Phone
- directly call phone numbers
- read phone status and identity
Camera
- take pictures and videos
Device ID & call information
- read phone status and identity
Calendar
- read calendar events plus confidential information
- add or modify calendar events and send email to guests without owners’ knowledge
Identity
- find accounts on the device
- add or remove accounts
- read your own contact card
Wi-Fi connection information
- view Wi-Fi connections
Photos/Media/Files
- read the contents of your USB storage
- modify or delete the contents of your USB storage
Device & app history
- retrieve running apps
Contacts
- find accounts on the device
- read your contacts
- modify your contacts
Storage
- read the contents of your USB storage
- modify or delete the contents of your USB storage
Location
- approximate location (network-based)
- precise location (GPS and network-based)
Other
- download files without notification
- receive data from Internet
- read TV channel/program information
- write TV channel/program information
- full network access
- read battery statistics
- run at startup
- draw over other apps
- control vibration
- modify system settings
- prevent device from sleeping
- send sticky broadcast
- pair with Bluetooth devices
- connect and disconnect from Wi-Fi
- install shortcuts
- read sync settings
- create accounts and set passwords
- view network connections
- toggle sync on and off
- control Near Field Communication
- access Bluetooth settings
- change your audio settings
- change network connectivity
- read Google service configuration
That’s quite a list! Some items in this list make sense, but you can assume these permissions are being used for nefarious reasons too. For example, under “Camera” there is the item “take pictures and videos”. Well, those are things you can share on Facebook so this makes some sense, especially if you use Facebook Live to broadcast a live video. Never mind that this also gives Facebook access to your camera at other times, too.
The camera is likely not an enormous deal in most instances, but what about the microphone access? You ever notice how you will talk to someone about a certain topic then login to Facebook and see an ad for that thing. Do you still think that’s a coincidence? Notice how it also has the permission to launch at startup which enables this level of privacy invasion?
There is a reasonably simple way to limit the permission these evil companies have to your mobile devices. The best thing you can do is avoid downloading the official app and visit these sites using a private web browser like Brave, Bromite, Vivaldi, etc. This way these apps don’t have that level of access to your device and their ability to track and spy on you is greatly limited.
You can even add browser shortcuts to your favorite social networks and websites right to your home screen so it feels like launching an app and you have quick access to it. You can see a tutorial for doing this on an Android device HERE. Even though it shows how to do this for a handful of the absolute worst browsers out there, the steps are mostly the same for Brave, Bromite, or any other Chromium-based browser. You can also find instructions for accomplishing this on iOS HERE, but I can’t speak to what browsers are available on iOS or if these instructions are super accurate.
Never Post Your Current Location
This should go without saying, but I know it needs to be said. DO NOT POST YOUR CURRENT LOCATION ONLINE! Revealing where you live makes you vulnerable to all kinds of attacks including robbery, home invasion, doxxing to a larger audience, stalking, harassment, and even selling your data to spammers for location-targeted spam.
When you aren’t at home and you post your location, you’re basically saying “go kick in my door and take my stuff because I’m not there”. I know, that sounds a little extreme, but it has happened and will continue to happen. Wait until you get home from your vacation to post your vacation photos all at once.
The Approach You Will Stick with is the Approach You Should Take
As usual, I’m going to leave you with the advice of picking what you will actually stick with and doing that. The best approach is the one you will be able to tolerate. If you go full tinfoil hat, you might find it too jarring and quickly stop your newly adopted privacy measures. We don’t want that. Instead, start small and build up to tinfoil hat mode if that is where you want to be.
I’m not going to say you have to leave these terrible social networks, but I do recommend you at least take some more steps to limit their access to the details of your life and possibly even consider trying a new social network that respects your privacy a bit more.